A CBDC, at a minimum, consists of a record of transactions (a ledger) and an interface to enable users to exchange currency. This core ledger, which should be stored in a secure environment, forms the basis of a CBDC and allows assets to be issued by a central bank. On top of this, other products, including for identity management and payment gateways will likely be necessary depending on the purpose of the CBDC.
Digital Ledger
The ledger’s role is to record central bank liabilities and enable the minting of digital currencies. It should be highly secure, available, resilient, fast, efficient, immutable, and interoperable for recording transactions at the cost of micropayments. This record represents the status of all issued central bank money.
Three common types:
• Traditional database
• WORM database
• Distributed ledger
Traditional database
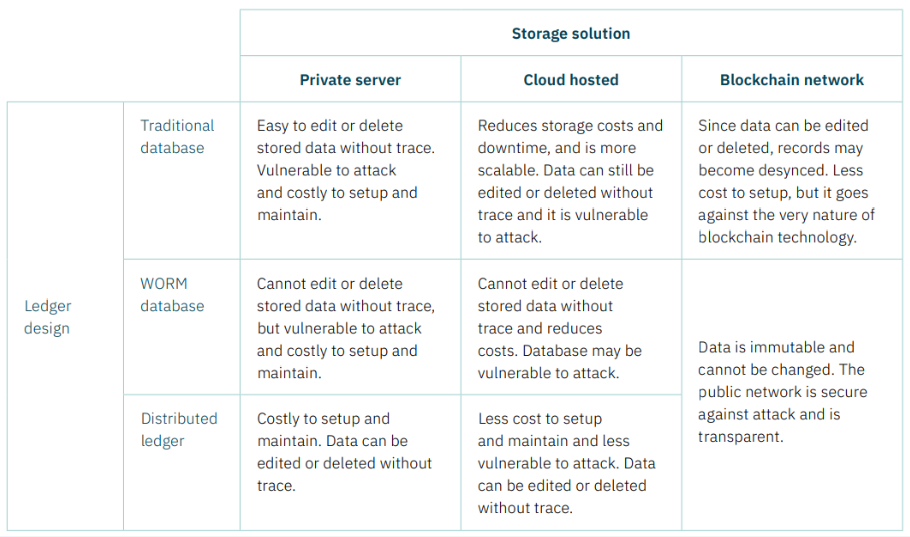
A CBDC could use a traditional database for the ledger of liabilities. Such a record can easily be manipulated and previous entries amended or deleted by malicious actors. This is therefore ill-equipped for widespread adoption by households and businesses, and not a suitable choice for a CBDC.
Worm database
Write once read many (WORM) systems, including, for example, Oracle-based databases, allow users to store data but not delete entries. CD-Rs share this quality. Immutability is critical for a CBDC, and in a WORM database, any updates to data entries are instead appended. This is similar to blockchain technology and inherently more secure than traditional databases. WORM databases form the backbone of modern accounting software, often deployed across large-scale industries. Such systems solve the problem of mutability and malicious data manipulation, but since there is only a single copy of a WORM database, data loss is an inherent risk.
Distributed ledger
A distributed ledger is most often associated with CBDC implementations. Examples include BitcoinSV, Ethereum and Hyperledger.
Distributed ledgers may be either private or public. As the name suggests, the record of transactions is shared across multiple instances, rather than stored in a single place.
Data is replicated and synchronised between several entities without the need for a central administrator, making the record more secure against potential attackers. Blockchains, for instance, time-stamp entries of transactions that can be conducted peer-to-peer. This allows transactions to be sent directly from one party to another and then settled on-chain, without going through a financial institution.
Double-entry bookkeeping
Like paper-based double-entry bookkeeping ledgers if any records must be updated or errors corrected, values can be added. The difference is that on the blockchain, values, including errors, cannot be deleted and remain in the record even after corrections. This is to ensure the integrity of data, particularly when being updated and amended. Token systems overlaid on top of the blockchain can give central banks control of the number and allocation of tokens for government-backed money like a CBDC.
3 important components are used in distributed ledgers like blockchains:
I. Digital signatures
Private-public key pairs present a way to perform transactions between two parties. For high-value transactions, each participant can use such keys pairs to produce a secure digital identity reference, using certificate authorities and public key infrastructure. The issue of identity forms one of the most important aspects of blockchain technology.
2. Peer-to-peer communication
Users or clients of the network can engage peer-to-peer, handing transactions directly to one another, before being settled on-chain. All transactions are pseudonymous, maintaining privacy, yet traceable.
3. Public distribution
When a transaction is authorised, transactions are publicly announced and broadcast across the entire network, making double-spending infeasible. Users can easily query the status of their own transactions and ensure integrity in the order of transactions.
Node operators
In a blockchain network, node operators publicly announce authorised transactions and update the blockchain – forming the ledger of central bank liabilities – through the creation of blocks. The miner who wins the right to confirm a transaction and add it to the blockchain must confirm the integrity and validity of the requested transaction, including that the digital cash to be spent has not already been spent, and abide by other rules of the protocol.
Storage Solution
The digital ledger must be stored. This can be done using a private or closed network, or a public network.
Three common types:
• Private server
• Cloud storage
• Blockchain network
Private server
The most basic storage solution is to store the CBDC ledger on a closed network, for which access is restricted. This means it would use an on-site, privately-owned server – not the cloud – that is controlled by a central bank. Private servers can be costly to set up and maintain, and are vulnerable to both attack and system outages. Using this method to save the database of transactions is not recommended, since it is far less secure. Actors can exert direct control over the protocol of, and data stored using, the underlying network.
Any compromise of such entities presents a potential compromise of the system and the data stored therein. Crucially, transaction data can be deleted without leaving a record of the change, allowing malicious actors to cover their tracks, and limiting the ability to hold parties accountable. Such inherent characteristics make it easier for malicious actors to retain their anonymity and make it more difficult to comply with anti-money laundering (AML) directives and know your customer (KYC) guidelines.
Cloud storage
Storing the CBDC ledger in the cloud, using a service such as Microsoft Azure, Amazon AWS, or Google Cloud, would allow a central bank to reduce fixed costs of running a private server, while also providing the flexibility to scale where necessary. Installing and maintaining server infrastructures can be expensive and requires specific expertise. Amazon claim some key benefits of a cloud architecture setup would be disaster resiliency, security, and throughput. Central banks may employ the services of multiple cloud providers as an insurance against the risk that one fails. While efficiencies by and large have improved, cloud infrastructure remains expensive for small casual transactions, or any exchange of small sensitive data – and can be prone to data security issues.
An exposed vulnerability in Microsoft Azure’s flagship Cosmos DB database in August 2021 meant that potential malicious actors could have obtained keys that controlled access to databases held by thousands of companies. This has raised concerns over consumer privacy – critical for a CBDC – as well as over the fact that large systems would lie in the hands of private cloud providers and corporations. Cloud infrastructure seems therefore less suitable as critical infrastructure for a widespread payment network.
Blockchain network
The ledger can also be stored on a blockchain network. Blockchain technology therefore refers to both the record of transactions (distributed ledger) as well as the storage solution (the public network). In this design, transactions are announced publicly to the network and are therefore visible, though pseudonymous, by everybody. Each node has an exact copy of the ledger. This makes blockchain uniquely transparent and immutable. It is important to clarify that many distributed ledger software operate on private networks, including Hyperledger, Ripple, Quorum, and Corda.
Although these share a similar design to a blockchain, since both consist of multiple nodes that hold a copy of the record, access to the nodes is restricted since they are hosted in closed networks on the cloud or on private servers. This negates much of the benefit offered by blockchain technology, and such a setup also lacks any inherent ongoing incentive for improvement and innovation beyond the initial investment, by discouraging competition. A public network such as a blockchain is ideally suited to host the ledger of transactions or central bank liabilities.
Comparing the technology
Interface
A digital wallet, accessed usually using a mobile phone or internet browser, is the most obvious point of connection for users wanting to exchange currency in a retail CBDC. This allows true peer-to-peer exchange between individuals, or even merchants and businesses.
Wallets can simplify and mirror the current digital payment infrastructure where citizens might have their bank card or PayPal saved on a smartphone. The difference is that in a CBDC, peer-to-peer transactions can be settled instantly, and do not require recipients to be online.
Where the penetration of smart phones is low, it is possible to provide an interface to the CBDC via industry standard protocols such as Unstructured Supplementary Service Data (USSD) that can be supported by older GMS based devices.
To drive financial inclusion, it is also worth considering the role of smart cards where data connectivity is unavailable and there is a lack of access to mobile devices.
Apps
We define apps as any overlay software or gateways that interact with a CBDC ledger. Some of these, including identification management, will almost certainly form a necessary part of any CBDC design. Digital certificates/ID Identity and payments are closely linked.
A digital ID or e-Certificate, such as a digital passport, is likely essential for any CBDC if it is to provide benefits such as KYC and preventing illicit activities, including AML.
Permissioned CBDCs with tiered authorisation to access different data fields require robust identity management to ensure users – for example law enforcement – are who they say they are. Such a product allows tokenising, sharing, and managing identifiable data through certification and audibility.
The benefit of a blockchain, token-based CBDC is that an ID can incorporate any amount of sensitive information including health data, biometric data, or financial data; but do so in a way that protects user privacy by granting businesses and authorities viewing rights only of the essential information needed to, for example, process a transaction.
Payment APIs APIs to create interoperable digital payment systems that connect citizens, merchants, banks, and other financial providers to services such as VISA, Mastercard or foreign exchange. Other overlay software A programmable CBDC would allow for other overlay software to be built on top.
At nChain, we are working with central banks to research and design a truly more resilient, trusted and inclusive modern economy, securing the livelihoods and prosperity of citizens for generations to come.
Interested to learn more about CBDC? Download the Playbook or sign up to be the first to know about our CBDC Masterclass below.
CBDC Playbook
This 40-page comprehensive guide will help you understand how CBDC programs can be designed and implemented, and some of the key questions that need to be addressed to help ensure a successful CBDC implementation.
CBDC Masterclass Series
The nChain CBDC Tech Masterclass Series aims to provide both foundational principles, expert opinion and lively discussion around the technical considerations of CBDC and creating a more resilient payments system for all.